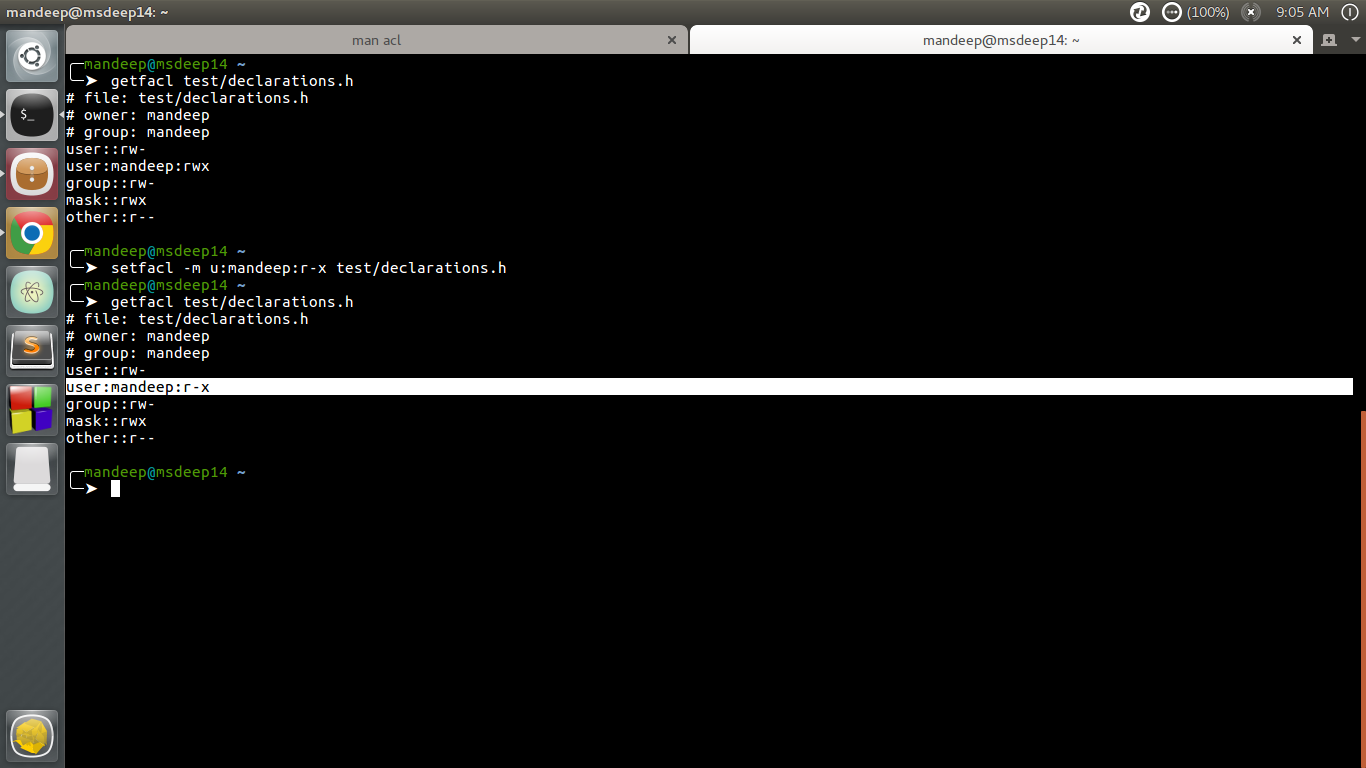
In today’s data-driven world, managing access to information is paramount for businesses of all sizes. Whether it’s sensitive financial data, proprietary intellectual property, or confidential customer information, ensuring that only authorized individuals have access to critical information is essential for protecting data integrity, maintaining regulatory compliance, and safeguarding against potential security threats. One effective way to manage access to information is by setting user and group permissions, which dictate who can view, edit, and share specific data within an organization’s digital ecosystem. In this article, we’ll explore the importance of managing access to information and provide practical tips for setting user and group permissions to enhance data security and governance.
Understanding User and Group Permissions
Before diving into the specifics of setting user and group permissions, it’s essential to understand the concepts behind them. User permissions refer to the rights and privileges granted to individual users within a system, while group permissions apply to predefined groups of users who share similar roles or responsibilities. By assigning permissions at both the user and group levels, organizations can efficiently manage access to information based on the principle of least privilege, ensuring that users have only the access they need to perform their job functions.
Benefits of Setting User and Group Permissions
Setting user and group permissions offers several benefits for organizations, including:
- Enhanced Security: By restricting access to sensitive information to only authorized individuals, organizations can mitigate the risk of unauthorized access and data breaches.
- Improved Collaboration: Group permissions allow teams to collaborate more effectively by providing access to shared resources and documents, streamlining workflows, and fostering collaboration across departments.
- Regulatory Compliance: Compliance with regulations such as GDPR, HIPAA, and SOX requires organizations to implement strict access controls and permissions to protect sensitive data and ensure data privacy and integrity.
- Efficient Resource Management: User and group permissions enable organizations to allocate resources more efficiently by granting access to specific tools, applications, and data based on users’ roles and responsibilities.
Practical Tips for Setting User and Group Permissions
Now that we understand the importance of managing access to information let’s explore some practical tips for setting user and group permissions effectively:
- Perform Regular Access Reviews: Regularly review and audit user and group permissions to ensure that access rights are up-to-date and aligned with users’ roles and responsibilities. Remove any unnecessary or outdated permissions to reduce the risk of unauthorized access.
- Follow the Principle of Least Privilege: Apply the principle of least privilege when assigning permissions, granting users and groups only the minimum level of access required to perform their job functions. Avoid granting excessive permissions that could potentially compromise data security.
- Implement Role-Based Access Control (RBAC): Use role-based access control to assign permissions based on users’ roles within the organization. Define roles with specific sets of permissions and assign users to appropriate roles based on their job functions and responsibilities.
- Use Groups to Simplify Permissions Management: Utilize groups to simplify permissions management and streamline access control. Assign permissions to groups rather than individual users whenever possible, making it easier to manage access rights across multiple users with similar roles.
- Centralize Permissions Management: Centralize permissions management using a dedicated access control system or directory service, such as Active Directory or LDAP. Centralized management ensures consistency and simplifies the process of granting, revoking, and updating permissions across the organization.
- Provide Training and Documentation: Educate users on the importance of access controls and provide training and documentation on how to manage permissions effectively. Encourage users to report any suspicious or unauthorized access attempts and provide channels for reporting security incidents.
Managing access to information is a critical aspect of data security and governance for organizations of all sizes. By setting user and group permissions effectively, organizations can enhance data security, improve collaboration, ensure regulatory compliance, and streamline resource management. By following the practical tips outlined in this article, organizations can establish robust access controls that protect sensitive information while enabling users to access the resources they need to perform their job functions effectively. With careful planning, implementation, and ongoing monitoring, organizations can create a secure and efficient digital environment that supports their business objectives and protects against potential security threats.